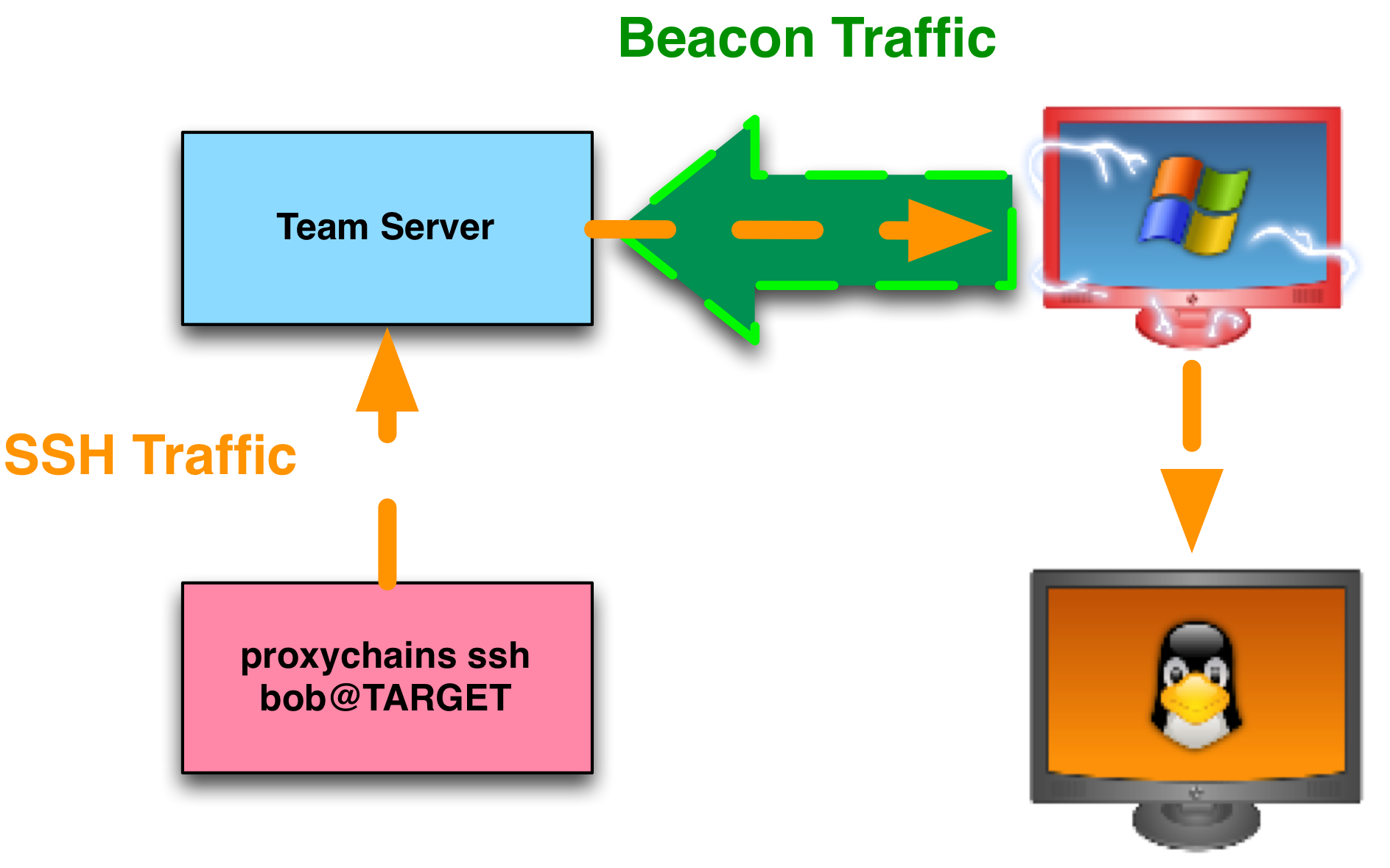
Socks Proxy Cobalt Strike . To learn more about proxychains, visit:. Cobalt strike’s beacon payload has had socks proxy pivoting since 2013. This is a quick note showing how to get an interactive remote desktop session (rdp) session from a cobalt strike beacon by. The target network is a compromised active directory environment where. Simply point the application at your cobalt strike team server, put in the right port, and away you go. Cobalt strike can facilitate all the above techniques and even rdp using socks proxy. My roadmap for cobalt strike 3.0 calls for a. This form of pivoting makes it easy to tunnel many tools. Cobalt strike has pivot listeners to expose the metasploit framework’s ability to relay payload connections through a pivot host. C2 will be a cobalt strike teamserver listening with a socks4a service. Smb/wmi executable transfer and exec according to our telemetry, this method is. Socks pivoting is also easy on.
from www.cobaltstrike.com
To learn more about proxychains, visit:. This is a quick note showing how to get an interactive remote desktop session (rdp) session from a cobalt strike beacon by. Simply point the application at your cobalt strike team server, put in the right port, and away you go. Cobalt strike can facilitate all the above techniques and even rdp using socks proxy. Socks pivoting is also easy on. Cobalt strike has pivot listeners to expose the metasploit framework’s ability to relay payload connections through a pivot host. C2 will be a cobalt strike teamserver listening with a socks4a service. My roadmap for cobalt strike 3.0 calls for a. Cobalt strike’s beacon payload has had socks proxy pivoting since 2013. Smb/wmi executable transfer and exec according to our telemetry, this method is.
Linux, Left out in the Cold? Cobalt Strike
Socks Proxy Cobalt Strike Cobalt strike can facilitate all the above techniques and even rdp using socks proxy. Cobalt strike can facilitate all the above techniques and even rdp using socks proxy. To learn more about proxychains, visit:. Smb/wmi executable transfer and exec according to our telemetry, this method is. Cobalt strike’s beacon payload has had socks proxy pivoting since 2013. My roadmap for cobalt strike 3.0 calls for a. This form of pivoting makes it easy to tunnel many tools. Cobalt strike has pivot listeners to expose the metasploit framework’s ability to relay payload connections through a pivot host. The target network is a compromised active directory environment where. Simply point the application at your cobalt strike team server, put in the right port, and away you go. C2 will be a cobalt strike teamserver listening with a socks4a service. This is a quick note showing how to get an interactive remote desktop session (rdp) session from a cobalt strike beacon by. Socks pivoting is also easy on.
From blog.nviso.eu
Cobalt Strike Using Known Private Keys To Decrypt Traffic Part 1 Socks Proxy Cobalt Strike Smb/wmi executable transfer and exec according to our telemetry, this method is. C2 will be a cobalt strike teamserver listening with a socks4a service. This is a quick note showing how to get an interactive remote desktop session (rdp) session from a cobalt strike beacon by. Cobalt strike’s beacon payload has had socks proxy pivoting since 2013. Cobalt strike can. Socks Proxy Cobalt Strike.
From fastestvpn.com
Here’s How SOCKS Proxy Differs from a VPN Socks Proxy Cobalt Strike Cobalt strike’s beacon payload has had socks proxy pivoting since 2013. C2 will be a cobalt strike teamserver listening with a socks4a service. Cobalt strike can facilitate all the above techniques and even rdp using socks proxy. Socks pivoting is also easy on. This form of pivoting makes it easy to tunnel many tools. The target network is a compromised. Socks Proxy Cobalt Strike.
From crawlbase.com
What is a SOCKS5 Proxy, and What is it Best for? Crawlbase Socks Proxy Cobalt Strike Socks pivoting is also easy on. Smb/wmi executable transfer and exec according to our telemetry, this method is. C2 will be a cobalt strike teamserver listening with a socks4a service. Simply point the application at your cobalt strike team server, put in the right port, and away you go. The target network is a compromised active directory environment where. Cobalt. Socks Proxy Cobalt Strike.
From www.cobaltstrike.com
Linux, Left out in the Cold? Cobalt Strike Socks Proxy Cobalt Strike Smb/wmi executable transfer and exec according to our telemetry, this method is. To learn more about proxychains, visit:. Socks pivoting is also easy on. Cobalt strike can facilitate all the above techniques and even rdp using socks proxy. My roadmap for cobalt strike 3.0 calls for a. Simply point the application at your cobalt strike team server, put in the. Socks Proxy Cobalt Strike.
From www.stupidproxy.com
How to Use 911 SOCKS Proxies Stupid Proxy Socks Proxy Cobalt Strike Simply point the application at your cobalt strike team server, put in the right port, and away you go. To learn more about proxychains, visit:. Cobalt strike’s beacon payload has had socks proxy pivoting since 2013. My roadmap for cobalt strike 3.0 calls for a. Cobalt strike can facilitate all the above techniques and even rdp using socks proxy. This. Socks Proxy Cobalt Strike.
From www.mandiant.es
Cobalt Strike Definición de los componentes de Cobalt Strike y BEACON Socks Proxy Cobalt Strike C2 will be a cobalt strike teamserver listening with a socks4a service. This is a quick note showing how to get an interactive remote desktop session (rdp) session from a cobalt strike beacon by. To learn more about proxychains, visit:. Smb/wmi executable transfer and exec according to our telemetry, this method is. My roadmap for cobalt strike 3.0 calls for. Socks Proxy Cobalt Strike.
From www.bleepingcomputer.com
Google releases 165 YARA rules to detect Cobalt Strike attacks Socks Proxy Cobalt Strike To learn more about proxychains, visit:. This is a quick note showing how to get an interactive remote desktop session (rdp) session from a cobalt strike beacon by. Cobalt strike has pivot listeners to expose the metasploit framework’s ability to relay payload connections through a pivot host. C2 will be a cobalt strike teamserver listening with a socks4a service. Smb/wmi. Socks Proxy Cobalt Strike.
From community.sophos.com
Detecting Cobalt Strike Announcements Sophos NDR Sophos Community Socks Proxy Cobalt Strike The target network is a compromised active directory environment where. Cobalt strike can facilitate all the above techniques and even rdp using socks proxy. This form of pivoting makes it easy to tunnel many tools. This is a quick note showing how to get an interactive remote desktop session (rdp) session from a cobalt strike beacon by. My roadmap for. Socks Proxy Cobalt Strike.
From github.com
GitHub SamSepiolProxy/CobaltStrikeScripts A collection of scripts Socks Proxy Cobalt Strike This is a quick note showing how to get an interactive remote desktop session (rdp) session from a cobalt strike beacon by. This form of pivoting makes it easy to tunnel many tools. Socks pivoting is also easy on. Cobalt strike can facilitate all the above techniques and even rdp using socks proxy. Simply point the application at your cobalt. Socks Proxy Cobalt Strike.
From favpng.com
Red Team Cobalt Strike Computer Servers Proxy Server Security Hacker Socks Proxy Cobalt Strike This form of pivoting makes it easy to tunnel many tools. Socks pivoting is also easy on. The target network is a compromised active directory environment where. Cobalt strike’s beacon payload has had socks proxy pivoting since 2013. Simply point the application at your cobalt strike team server, put in the right port, and away you go. C2 will be. Socks Proxy Cobalt Strike.
From hu.hailbytes.com
A SOCKS4 és SOCKS5 proxyszerverek használata névtelen böngészésre Socks Proxy Cobalt Strike To learn more about proxychains, visit:. This is a quick note showing how to get an interactive remote desktop session (rdp) session from a cobalt strike beacon by. This form of pivoting makes it easy to tunnel many tools. Cobalt strike has pivot listeners to expose the metasploit framework’s ability to relay payload connections through a pivot host. Smb/wmi executable. Socks Proxy Cobalt Strike.
From www.proxysp.com
SOCKS Proxy Primer What are They & Where to Buy? ProxySP Socks Proxy Cobalt Strike Cobalt strike has pivot listeners to expose the metasploit framework’s ability to relay payload connections through a pivot host. This form of pivoting makes it easy to tunnel many tools. C2 will be a cobalt strike teamserver listening with a socks4a service. Simply point the application at your cobalt strike team server, put in the right port, and away you. Socks Proxy Cobalt Strike.
From psawenaughty.weebly.com
Good socks5 proxy list psawenaughty Socks Proxy Cobalt Strike Simply point the application at your cobalt strike team server, put in the right port, and away you go. Smb/wmi executable transfer and exec according to our telemetry, this method is. To learn more about proxychains, visit:. This is a quick note showing how to get an interactive remote desktop session (rdp) session from a cobalt strike beacon by. Cobalt. Socks Proxy Cobalt Strike.
From tajdini.net
Cobalt Strike Defense Guide 2 Mahyar Notes Socks Proxy Cobalt Strike Cobalt strike has pivot listeners to expose the metasploit framework’s ability to relay payload connections through a pivot host. Socks pivoting is also easy on. To learn more about proxychains, visit:. This form of pivoting makes it easy to tunnel many tools. This is a quick note showing how to get an interactive remote desktop session (rdp) session from a. Socks Proxy Cobalt Strike.
From www.cobaltstrike.com
Reverse Port Forward through a SOCKS Proxy Cobalt Strike Socks Proxy Cobalt Strike Simply point the application at your cobalt strike team server, put in the right port, and away you go. This form of pivoting makes it easy to tunnel many tools. Cobalt strike’s beacon payload has had socks proxy pivoting since 2013. Cobalt strike has pivot listeners to expose the metasploit framework’s ability to relay payload connections through a pivot host.. Socks Proxy Cobalt Strike.
From thedfirreport.com
Cobalt Strike, a Defender's Guide Socks Proxy Cobalt Strike C2 will be a cobalt strike teamserver listening with a socks4a service. Smb/wmi executable transfer and exec according to our telemetry, this method is. The target network is a compromised active directory environment where. Cobalt strike can facilitate all the above techniques and even rdp using socks proxy. Socks pivoting is also easy on. Cobalt strike has pivot listeners to. Socks Proxy Cobalt Strike.
From medium.com
SOCKS 5 — A Proxy Protocol. Basically, SOCKS 5 is a Framework for a Socks Proxy Cobalt Strike Socks pivoting is also easy on. Cobalt strike has pivot listeners to expose the metasploit framework’s ability to relay payload connections through a pivot host. This form of pivoting makes it easy to tunnel many tools. This is a quick note showing how to get an interactive remote desktop session (rdp) session from a cobalt strike beacon by. C2 will. Socks Proxy Cobalt Strike.
From socksproxie.blogspot.com
Socks Proxies List USA Socks Proxy List Socks Proxy Cobalt Strike Smb/wmi executable transfer and exec according to our telemetry, this method is. Simply point the application at your cobalt strike team server, put in the right port, and away you go. Socks pivoting is also easy on. My roadmap for cobalt strike 3.0 calls for a. C2 will be a cobalt strike teamserver listening with a socks4a service. Cobalt strike’s. Socks Proxy Cobalt Strike.